Note: This is my write-up for one of the reverse engineering challenges in Cyber Security Challenge competition organized by iTREXC (4th International Innovation, Technology & Research Exhibition and Conference). This “Find Me” challenge is in Reverse Engineering category. The difficulty of this “Find Me” challenge is Easy.
For this “Find Me” challenge, we were given an APK file (android application package). We can use JADX-GUI and Android Studio to reverse and run this APK file. Opening the APK file in JADX-GUI tells us that there’s a Java Method (also known as function) named “encrypt” that encrypt a string using AES and Base64. We can see that the IV (Initialization Vector) and Secret Key (encryption key) used for AES encryption are encryptionIntVec and dryEncyptionKey.
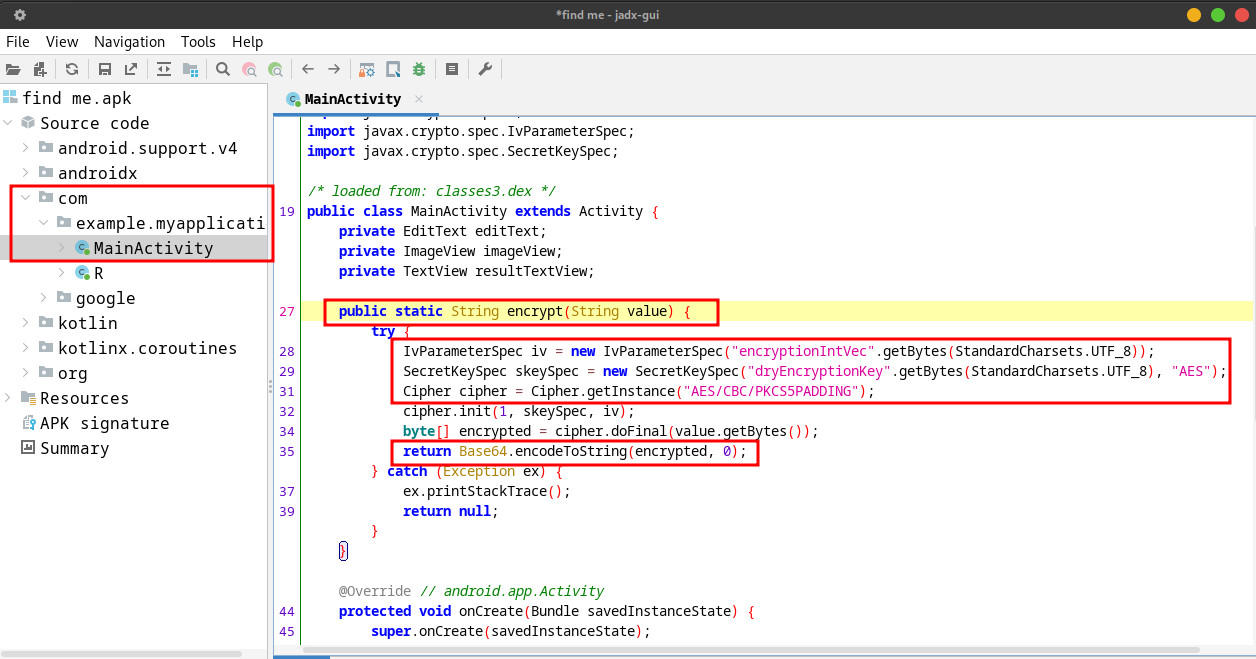
The application asked for user input in string format and stored that string in the “userAnswer” variable. The application then called the “encrypt” method above to encrypt the user input and stored that encrypted user input in the “EncUserAns” variable. The encrypted user input will then be compared with a hardcoded value : ABxl23A0HbfOIPvu3jHQ== (if both are equal, we will get the encoded string CPmcjAylgzOLbc4sILX8UaAYf3C4UHYtFBzAcJ/LBWI=; otherwise, the application will display the “Try again “ message).
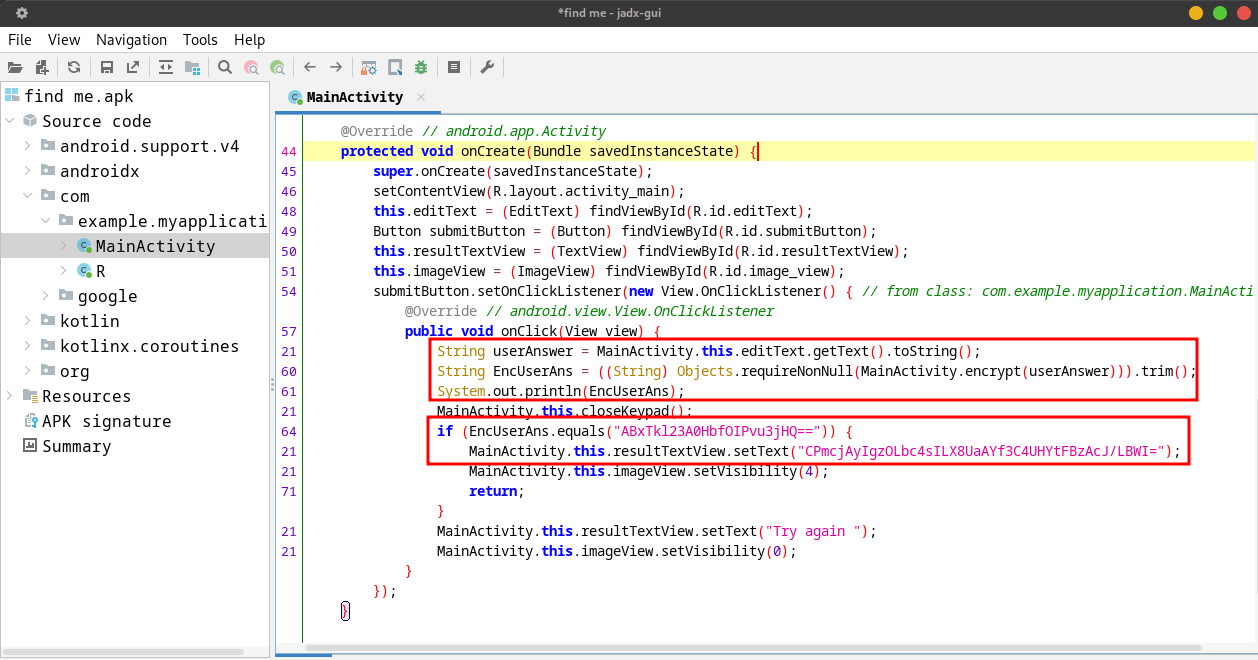
Decrypting ABxl23A0HbfOIPvu3jHQ== :
- Key : The secret key (encryption key) in UTF8 format.
- IV : The initialization vector in UTF8 format.
- Mode : CBC (Cipher Block Chaining)
- Input : Raw format
- Output : Raw format
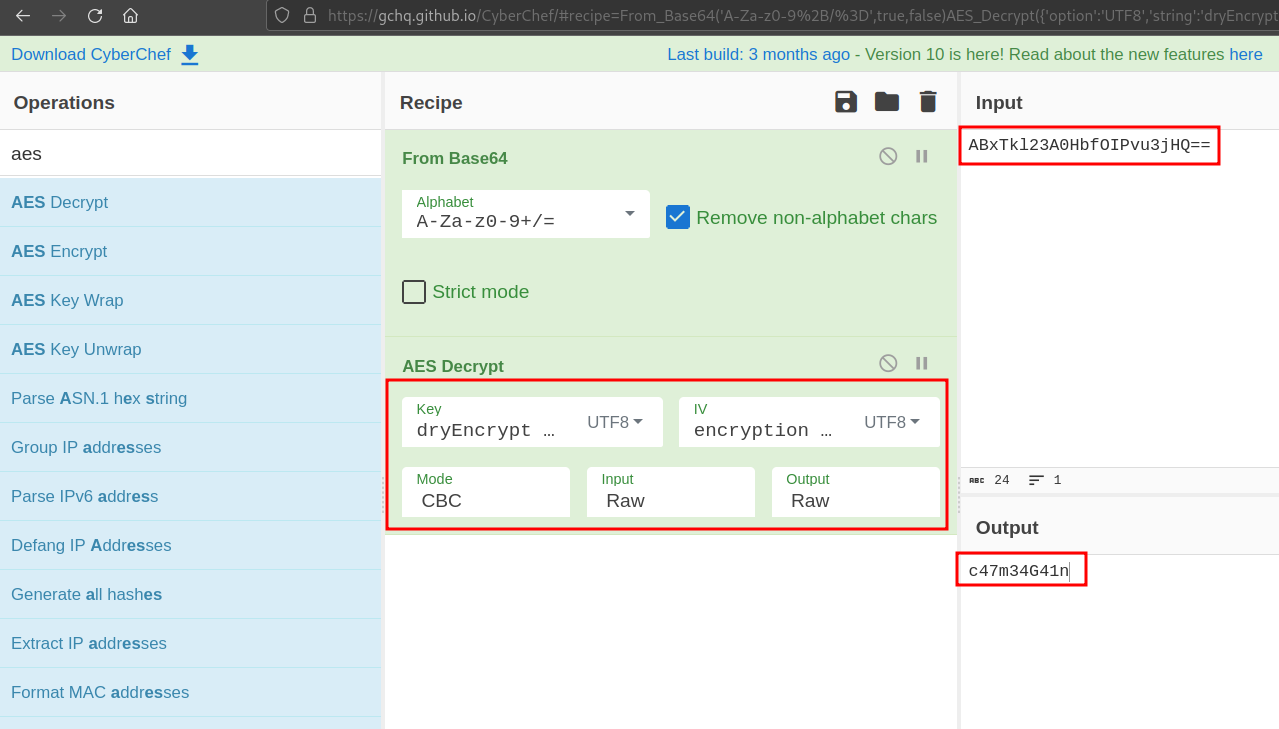
After decrypting the hardcoded value above, we know that the user input should be c47m34G41n. We can demonstrate this by running the application in Android Studio.
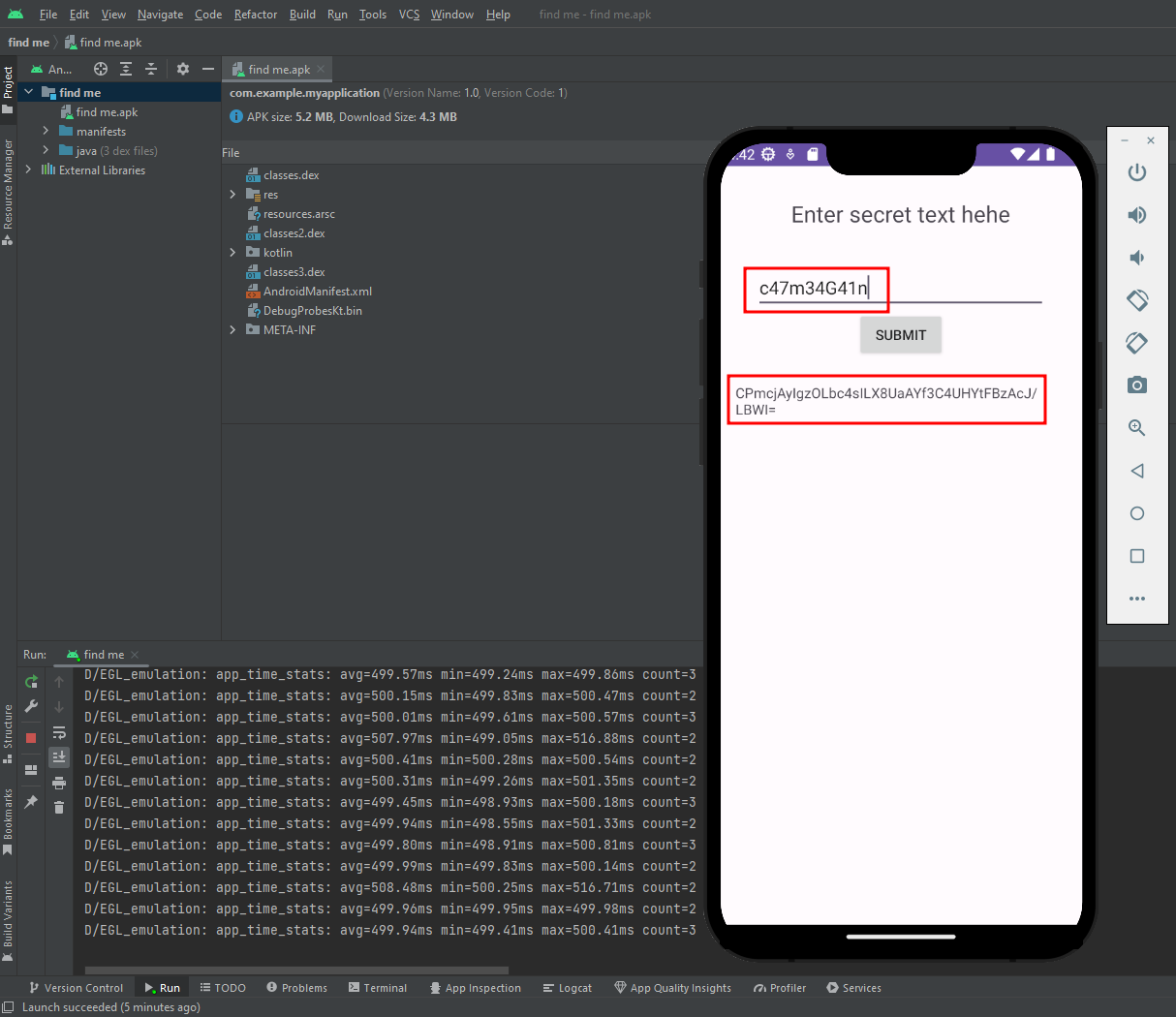
By using the same method to decrypt the hardcoded encrypted user input above, we can decrypt the encoded string :

After decrypting the encoded text, we get the flag : uisctf{aes_is_easy}.