Note: Understanding the OSI model is fundamental to grasping how computer networks and communication systems work. As you continue your studies and gain more experience in networking, you will likely encounter various scenarios where the OSI model’s concepts come into play. From time to time, you will understand more about the OSI model’s concepts. For example, you will understand how data from the application layer is encapsulated into various headers as it travels down the layers and how each layer adds its own information to the data.
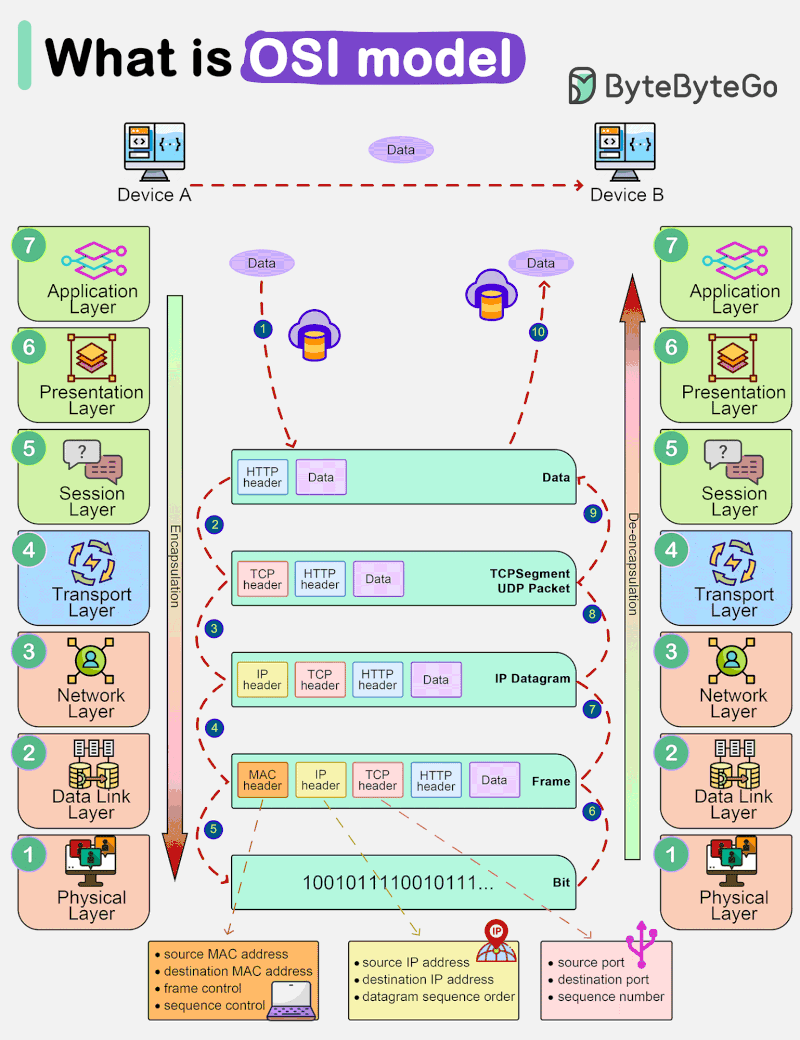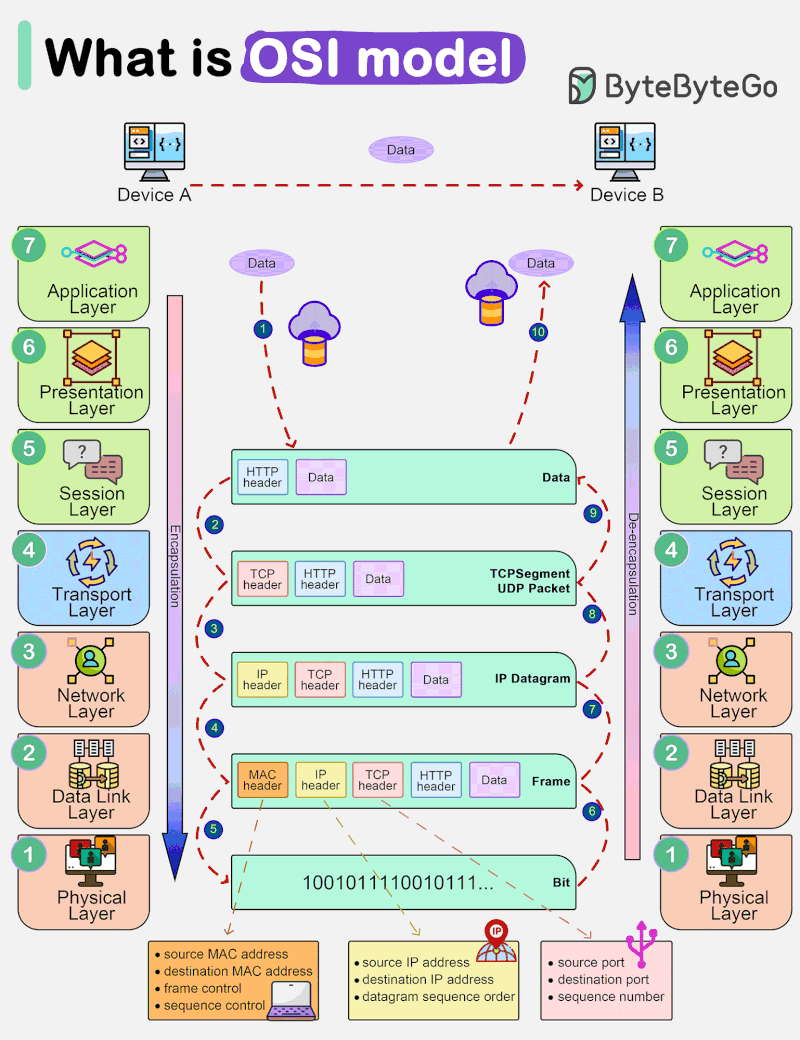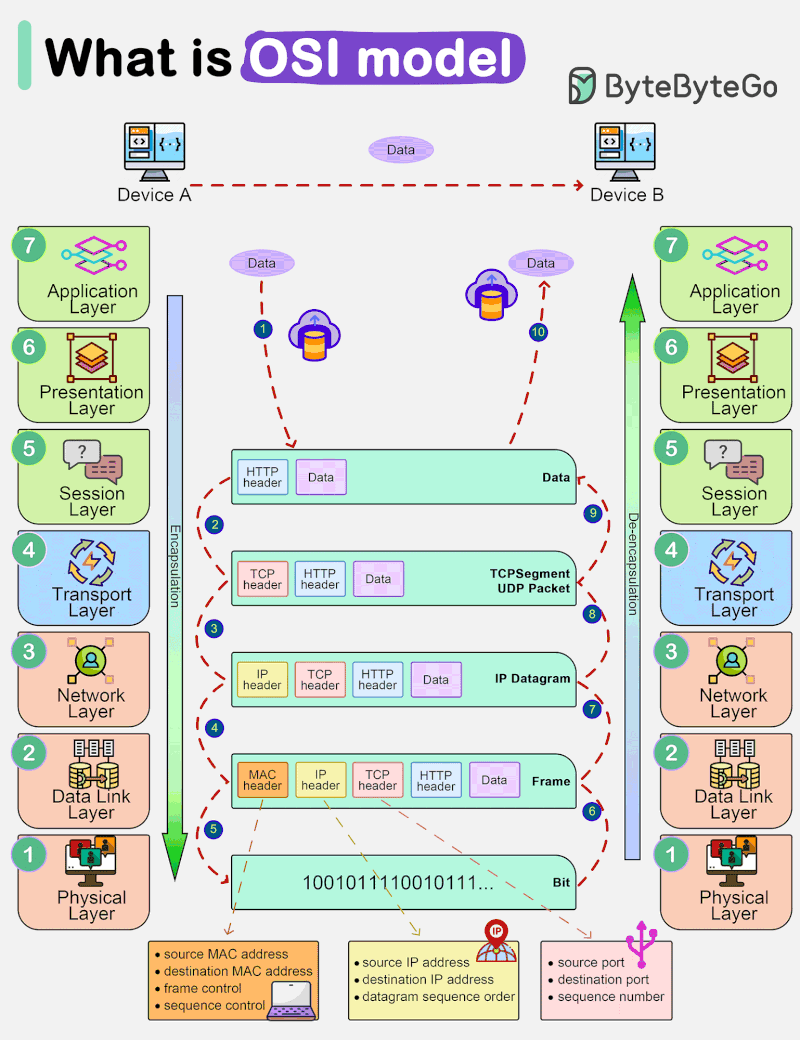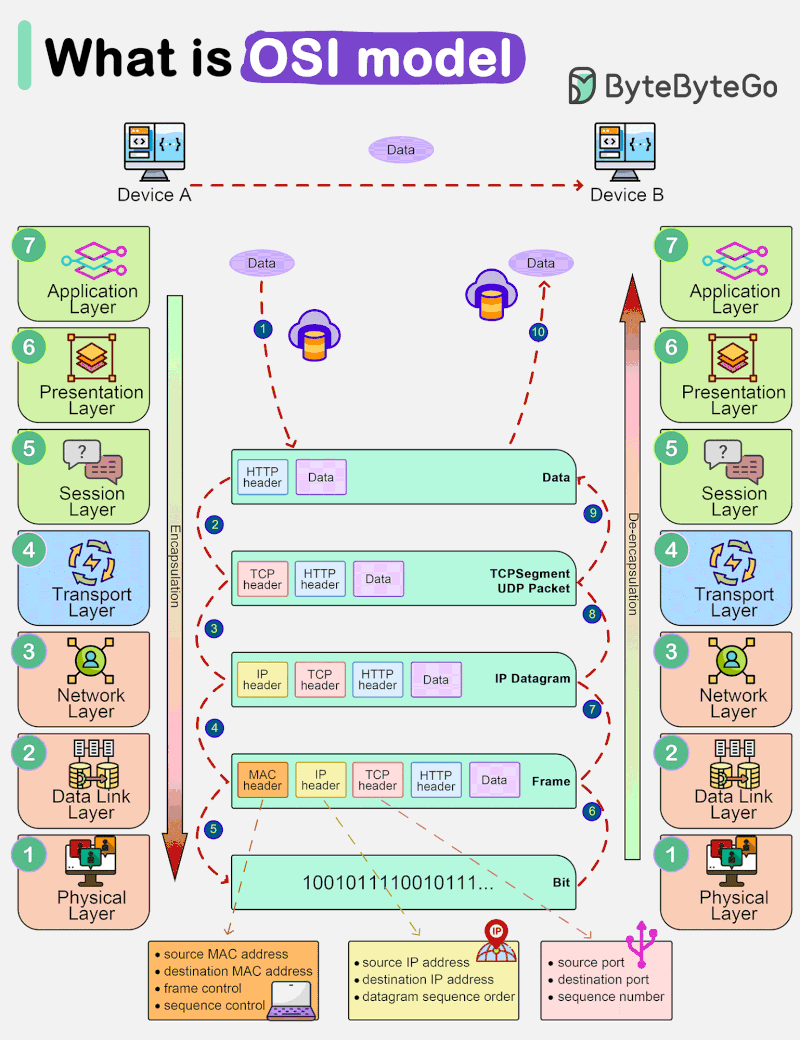
OSI model, which stands for Open Systems Interconnection model, is a conceptual framework that standardizes the functions of a telecommunications system into seven distinct layers. These layers help us understand how different networking protocols and technologies interact with each other to enable communication between devices.
The OSI model is a theoretical framework that helps us understand networking concepts more easily. In reality, networking protocols and technologies often don’t strictly adhere to the OSI model, and they may combine functionalities from multiple layers.
When troubleshooting network issues, understanding the OSI model can be extremely helpful. By understanding which layer might be causing a problem, we can narrow down the problem to a specific layer and focus our efforts on the appropriate area.
Layer 1 : Physical Layer
The lowest layer deals with the physical connection between devices. It defines the hardware specifications, such as cables, switches, and network interface cards (NICs). This layer is responsible for transmitting raw bits over the physical medium. This is the layer where the data gets converted into a bit stream, which is a string of 1s and 0s. The physical layer of both devices must agree on a signal convention so that the 1s can be distinguished from the 0s on both devices.
Layer 2 : Data Link Layer
This layer provides error detection and correction, ensuring reliable data transfer between directly connected devices, such as switches and network adapters. It is responsible for organizing raw data into frames and managing access to the physical medium using techniques like MAC addresses. Data link layer facilitates data transfer between two devices on the same network.
Layer 3 : Network Layer
The network layer is all about routing data packets across multiple networks. It deals with logical addressing (such as IP addresses) and determines the best path for data to reach its destination using routing algorithms. Network layer facilitates data transfer between two different networks. If the two devices communication are on the same network, then the network layer is unnecessary. Data link layer and network layer are responsible for flow control and error control in intra-network communication. Network layer protocols include :
- IP (Internet Protocol)
- ICMP (Internet Control Message Protocol)
- IGMP (Internet Group Message Protocol)
- IPsec (Internet Protocol Security)
Layer 4 : Transport Layer
This layer handles end-to-end communication between devices. It ensures that data is delivered reliably and in the correct order. Transport layer is responsible for flow control and error control for inter-network communication. Transport layer protocols include :
- TCP (Transmission Control Protocol)
- UDP (User Datagram Protocol)
Layer 5 : Session Layer
The session layer establishes, manages, and terminates (opening and closing) communication sessions between applications on different devices. The time between when the communication is opened and closed is known as the session. The session layer ensures that the session stays open long enough to transfer all the data being exchanged, and then promptly closes the session in order to avoid wasting resources. It also helps in the synchronization and checkpointing of data exchange.
Layer 6 : Presentation Layer
This layer is responsible for data translation and encryption, ensuring that data from the application layer of one system can be understood by the application layer of another system. This layer is primarily responsible for preparing data so that it can be used by the application layer. In other words, presentation layer makes the data presentable for applications to consume. Two communication devices may be using different encoding methods, so presentation layer is responsible for translating incoming data into a syntax that the application layer of the receiving device can understand. If the devices are communicating over an encrypted connection, presentation layer is responsible for adding the encryption on the sender’s end as well as decoding the encryption on the receiver’s end, so that it can present the application layer with unencrypted, readable data. It also takes care of data compression and decompression.
Layer 7 : Application Layer
The topmost layer is the only layer that directly interacts with end-user applications and provides network services directly to them. Software applications like web browsers and email clients rely on the application layer to initiate communications. But it should be made clear that client software applications are not part of the application layer; rather, the application layer is responsible for the protocols and data manipulation that the software relies on to present meaningful data to the user. Common application layer protocols include :
- HTTP (Hypertext Transfer Protocol)
- FTP (File Transfer Protocol)
- SMTP (Simple Mail Transfer Protocol)
- DNS (Domain Name System)
Flow Control & Error Control
- Flow control is a mechanism used to manage the rate of data transmission between a sender and a receiver to ensure that the receiving end can handle the incoming data without being overwhelmed. The goal of flow control is to prevent data loss, buffer overflows, and congestion in the network. Flow control determines an optimal speed of transmission to ensure that a sender with a fast connection does not overwhelm a receiver with a slow connection.
- Error control, also known as error detection and correction, is a mechanism used to identify and rectify errors that occur during data transmission over a network. Error detection process involve adding extra bits to the data being transmitted, which are called checksums or parity bits. The receiver uses these bits to detect errors in the received data. If an error is detected, the receiver can request the sender to retransmit the data. Some error control mechanisms not only detect errors but also have the capability to correct them. Techniques like Forward Error Correction (FEC) use additional redundant data to recover lost or corrupted bits at the receiver’s end without requesting retransmission. Errors can happen due to various reasons, such as noise in the communication channel, interference, or hardware issues.
Protocols such as TCP incorporate both flow control and error control mechanisms to ensure reliable and accurate data transmission across the network. These mechanisms play a crucial role in maintaining data integrity and a smooth communication experience for users and applications.